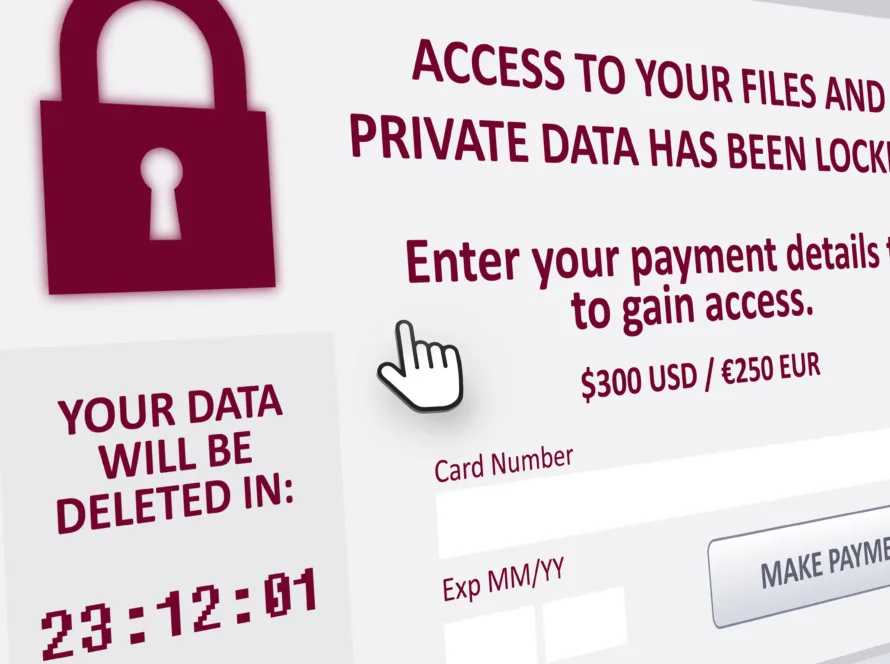
In today’s interconnected digital landscape, where technology is an integral part of our daily lives, the threat of malware looms large. Malware, short for malicious software, encompasses a variety of digital threats designed to infiltrate and damage computer systems, often without the user’s knowledge. Among the myriad forms of malware, one of the most insidious is the prevalence of scams. These scams have become a silent intruder, lurking in the shadows of the internet, waiting to prey on unsuspecting victims.
The Rise of Malware Scams
Malware scams have proliferated in recent years, capitalizing on the vulnerabilities of individuals and organizations alike. These scams are sophisticated ploys crafted to deceive users into divulging sensitive information or unwittingly downloading malicious software. From phishing emails purporting to be from reputable institutions to fraudulent websites masquerading as legitimate businesses, the tactics employed by cybercriminals are varied and ever-evolving.
Methods Used in Malware Scams
One of the primary methods utilized in malware scams is phishing. Phishing emails are crafted to appear as though they are from a trustworthy source, often prompting recipients to click on a link or provide personal information. Similarly, fake websites are designed to mimic the appearance of legitimate sites, tricking users into entering sensitive data.
Social engineering tactics are also commonly employed in malware scams. Cybercriminals exploit human psychology, leveraging techniques such as fear or urgency to manipulate individuals into taking actions that compromise their security.
Impacts of Malware Scams
The consequences of falling victim to malware scams can be severe and far-reaching. Financial loss is a common outcome, as cybercriminals may gain access to bank accounts or credit card information. Additionally, identity theft is a prevalent concern, with personal data being used to commit fraud or other crimes. Moreover, the damage to one’s reputation resulting from a malware attack can be difficult to repair, both personally and professionally.
Protecting Yourself from Malware Scams
In light of the pervasive threat posed by malware scams, it is imperative for individuals and organizations to take proactive measures to safeguard their digital assets. This includes keeping software updated to mitigate vulnerabilities and using strong, unique passwords for online accounts. Furthermore, exercising caution when interacting online, such as verifying the authenticity of emails and websites, can help prevent falling victim to scams.
Importance of Cybersecurity Awareness
Cybersecurity awareness plays a crucial role in combatting malware scams. By educating oneself and others about the risks associated with online activity, individuals can better recognize and respond to potential threats. Additionally, reporting suspicious activity to relevant authorities or cybersecurity professionals can help disrupt the operations of cybercriminals.
The Role of Technology in Combating Malware Scams
Advancements in technology have also contributed to the fight against malware scams. Antivirus software, firewalls, and multi-factor authentication are among the tools available to bolster digital defenses and thwart potential attacks. By leveraging these technological solutions, individuals and organizations can bolster their cybersecurity posture and mitigate the risk of falling victim to malware scams.
Conclusion
In conclusion, malware scams represent a pervasive and ever-present threat in the digital world. With cybercriminals continuously devising new tactics to exploit vulnerabilities, it is incumbent upon individuals and organizations to remain vigilant and proactive in their approach to cybersecurity. By staying informed, adopting best practices, and leveraging technological solutions, we can collectively combat the silent intruder that is malware.
*Fallen a victim to scams?
*Want to rerport a scam?
Look no futher than ReclaimLTD! Click here to open the main page>
FAQ
What is malware?
Malware, short for malicious software, refers to any software intentionally designed to cause damage to a computer, server, client, or computer network.
How do malware scams differ from other types of malware?
Malware scams typically involve deceptive tactics aimed at tricking users into divulging sensitive information or downloading malicious software, whereas other types of malware may focus on causing direct harm to computer systems.
What are some signs that an email or website may be part of a malware scam?
Signs of a malware scam include suspicious or unexpected emails requesting personal information, urgent messages prompting immediate action, and websites with irregular or misspelled URLs.
What steps can individuals take to protect themselves from malware scams?
Individuals can protect themselves by keeping software updated, using strong passwords, being cautious when clicking on links or downloading attachments, and verifying the authenticity of emails and websites.
How can technology help combat malware scams?
Technology such as antivirus software (e.g. McAfee), firewalls, and multi-factor authentication can help detect and prevent malware scams by identifying and blocking suspicious activity before it can cause harm.